How to launch a Security Token Offering (STO) is a series of posts taken from the Ebook we published in January, Tokenized Securities. It is a straight forward and comprehensive guide that walks issuers through the main steps involved in the process of launching a Security Token Offering (STO).
In part one, we introduced the topic area and defined tokenization. We highlighted the difference between utility tokens and security tokens in part two. In this article, we will discuss compliance aware tokens. With STOs, we are talking about securities and we need to ensure the transfer of these security tokens are performed in a compliant manner. Later, we will publish another article on the benefits of tokenization.
Typically, when a security token transfer occurs on a blockchain, the source address calls the smart contract transfer function. In its most basic form, this function has a destination address and an amount to transfer. However, for a STO to be issued in a legal manner, transfer instructions need to be programmed into the token to ensure compliance in every jurisdiction the offering is issued in:
Permissioned tokens
Permissioned tokens work with a validator or regulation service which will validate whether or not a trade should have the permission to be executed. In permissioned tokens the securities rules are coded into the token and the validator which can be centralized or decentralized. There are several open source smart contract templates (so called “protocols”) for permissioned tokens, the main ones are overwriting the “transferfrom” functions of the ERC20 token standard, and ask permission from a validator/regulator service, which may or may not be included in the protocol.
Identity management
To enforce the compliant trading of tokens it is of course important to execute the transfer between one wallet and another. However, as issuing securities implies respect to strict offering and secondary market rules, and as AML and KYC regulations apply, it is also fundamental to allow for the creation and management of identities for every stakeholder. Using protocols like the ERC-725/735 allows for a unique identity for a person or group that can be published and managed via the blockchain and allow for the identity to hold keys and sign actions. It provides an easier way to operate the lifecycle management of a token by identifying more easily who can and cannot make transfers and allow for multiple people within an organization to sign off on transactions if they have the necessary identity keys.
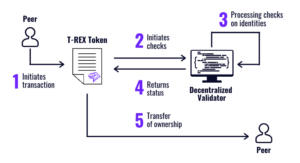
T-REX (Token for Regulated EXchanges)
To ensure compliance from the issuance of security tokens to their lifecycle management (securities servicing and transfers), issuers can use the open source T-REX (Token for Regulated EXchanges) infrastructure. This set of on-chain solutions is used to create compliant-by-design security tokens by respecting market standards and well tested smart contract templates. The T-REX ensures continuity with regards to KYC and AML compliance checks, ensuring all participants are eligible for the investment. It ensures interoperability with the main liquidity providers and allows issuers to allocate tokens to their investors and shareholders. The T-REX can easily be completed by other smart contracts and dApps to manage taxes and to conduct post-issuance corporate actions such as dividend payments, voting and announcements.
Only the T-REX suite of blockchain tools assembles onchain identities and permissioned tokens to guarantee transfers of ownership in a built-in validator service:
This content is inspired by the Ebook Tokenized Securities. Click here to download.
