How to launch a Security Token Offering (STO) is a series of posts taken from the ebook we published in January, Tokenized Securities. The ebook is a comprehensive guide that walks issuers through the main steps involved in the process of launching a STO.
In the first article, we introduced the topic area and defined tokenization. As promised, this time we are going to look at the difference between utility tokens and security tokens. Later on, we will publish another blog on compliance aware tokens.
To precisely define security tokens, let’s define something they are not, utility tokens. An ICO is a way to raise funds for a distributed network. A company, or a foundation, issues tokens that can be used by contributors to redeem a service the entity is offering. For example, if the issuer of the token is a company launching a decentralized car sharing platform, each kilometer of travel could be represented with a token. The tokens are a way to exchange value between participants of the network by representing a unit of service. As such, they are called utility tokens.
However, if the main purpose of the token is to generate an increase of monetary value for its holder, it is an investment and therefore will be considered a security in most jurisdictions. Obviously, if the issuer needs to collect funds in order to finance a company in the form of debt or equity, or if an asset manager wants to issue an investment fund, the token representing these financial instruments won’t be utility tokens, they are representations of securities and are therefore called security tokens. The key difference here is that utility tokens represent a right to use a predefined good or service. Security tokens represent a right to future financial flows resulting from the main activity of the issuer of the token. Here are some other key differences between the two:
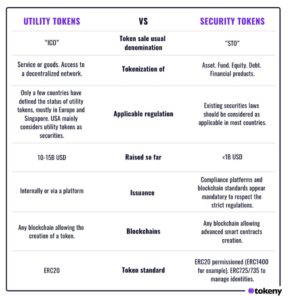
This content is inspired by the ebook Tokenized Securities. Click here to download.
